SOC 2
Implementation & Certification
System and Organisation Controls (SOC) reporting
SOC 2 Implementation & certification
SOC 2 stands for “System and Organization Controls 2” and is a framework developed by the AICPA (American Institute of Certified Practicing Accountants) to assess how organizations manage customer data security, with the compliance being verified through audits conducted by accredited businesses.
Digital transformation
Many, if not all, organizations are experiencing rapid digital transformation. While this evolution has enhanced operational efficiency and unlocked opportunities for growth and innovation, it has also introduced heightened vulnerabilities and security challenges, particularly in cloud-based data management. SOC 2’s comprehensive framework for risk management and data protection is increasingly essential in addressing these concerns.
SOC 1 vs SOC 2
SOC 1 (formerly SAS 70) is an audit report specifically addressing the security of financial statements, with international variants including ISAE 3402 or ASAE3402 report – international and Australian standards respectively. For SOC 1 reports, the AICPA requires auditors to be Certified Public Accountants (CPAs) licensed in the United States.
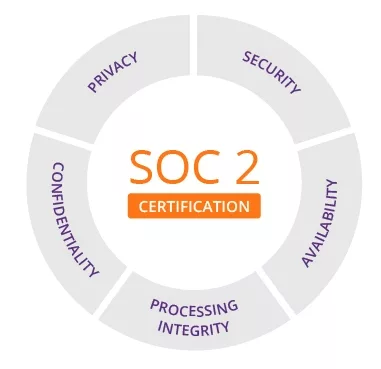
SOC 2 is a comprehensive audit report designed for organizations handling sensitive information, offering assurance regarding the security, availability, processing integrity of systems, and the confidentiality and privacy of the data managed or stored.
What's the difference - SOC 2 type 1 vs Type 2
There are two different types of AICPA SOC 2 attestation reports:
- A SOC 2 Type 1
- A SOC 2 Type 2
Both are valuable and serve a specific purpose, so you’ll need to decide which attestation report you need before starting the audit process. The requirement for either type 1 or type 2 can be driven specifically by demands from industry, regulators or customers.
Organizations often opt for a Type 2 attestation report when adopting SOC 2 as an organizational standard, as it provides a more robust evaluation of ongoing adherence to the framework over a specified period.
SOC 2 Type 1 compliance evaluates an organization’s cybersecurity controls at a single point in time.
The goal is to determine whether the internal controls put in place to safeguard customer data are sufficient and designed correctly.
Type 1 audits and reports can be completed in a matter of weeks.
SOC 2 Type 2 report examines how well a service organization’s system and controls perform over a period of time (typically 3-12 months).
What is their operating effectiveness? Do they function as intended?
Type 2 audits can take 12 months to complete and are more expensive than Type 1 audits.
Get your free trial today!
Protection against cyber threats both visible and those hidden “outside the flags !”