PCI DSS QSA
Ingressum can assist your organisation become PCI DSS Compliant (Payment Card Industry Data Security Standard) if you process, store or transmit credit card payments.

What is PCI DSS ?
PCI DSS, is jointly released by credit card companies aimed at protecting card holder data. The standard requires the members, merchants, and service providers using credit card facilities to carry out regular PCI Scans and PCI Security Audits after implementing the standard.

PCI DSS Requirements
Requirements of the standard – The PCI DSS version 3.2.1 is comprised of six control objectives that contain one or more requirements. In all there are 12 specific requirements under these control objectives. The verification and reporting process may vary depending on the level of merchants and service providers. An organization is also expected to identify its category or type for identifying what requirements are applicable to it.

ESTABLISH RESPONSE CAPABILITIES
Implementing security mechanisms across process control systems is not a one off exercise. Threats to the security and operation of process control systems develop and evolve over time and organisations should therefore undertake continuous assessment of process control system security.
Ingressum helps organizations meet all the requirements with the help of its robust consulting methodology
Ingressum
Secure the Network
Build and Maintain a secure network: Installing, configuring, and providing guidance on maintaining firewalls, intrusion detection and prevention systems, anti-virus and anti-spyware solutions. Reconfiguring default installations and customizing the setup. Conduct regular internal and external vulnerability assessments
Protect Card Holder Data
Protect Card Holder Data: Identifying the storage, transit channel, transit method, archival and retrieval of credit card data and securing the same. Identifying and implementing the appropriate controls at each data interface and data container
Regular Vulnerability Assessments
Maintain a Vulnerability Management Program: Conduct regular vulnerability identification, assessment and reporting exercises with fix implementation
Strong Access Control
Implement Strong Access Control Measures: Identify all logical and physical access points and ensure the access controls are present as per the requirement of the standard. Ensuring independent and reliable authentication and authorization schemes exist for access control
Regularly test everything
Regularly Monitor and Test Networks: Devise processes to regularly maintain and track network and data access and report any incidents in due time via a risk management procedure
Maintain Security Policies
Maintain an Information Security Policy: Draft and maintain a well-defined information security policy which addresses all the prerequisities of the standard.
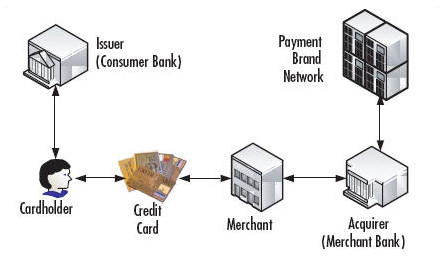
A typical cycle of credit card information touch points is shown in the diagram below:
Get your free trial today!
Protection against cyber threats both visible and those hidden “outside the flags !”