Secure Workspace
Cyber focused IT services for Microsoft O365
Ingressum’s Secure Workspace offers customers a hardened Microsoft environment, built with best practice security measures embedded to elevate both security and productivity.
Our Secure Workspace responds to the demand for increased cybersecurity for small-to-medium business among evolving external threats and the widespread adoption of remote work.
We merge Microsoft’s Office productivity suite, Identity, Access and Risk Management with a comprehensive array of advanced technologies and strict security frameworks to increase cyber resilience throughout the organisation.
Enhanced Productivity and Data Protection
Secure Workspace - seamlessly integrates best-in-class technologies, creating a bespoke and reliable environment tailored to elevate your organization's security and productivity.
Designed on a Strong Security Foundation
Secure Workspace is not merely a security solution – it’s a comprehensive approach that safeguards sensitive data, propels collaboration, and boosts productivity, laying the foundation for cyber resilience and organizational success amid evolving technical changes and advanced cyber threats.
It is designed on the fundamentals of a zero trust architecture (ZTA), mapped to Microsoft’s Security Architecture Framework and underlying technology stack and evaluated against the Australia Signals Directorate Essential Eight prioritised mitigation strategies.
And with ALL the elements expected in IT services
Microsoft
Leverage the collaboration of the entire Office 365 productivity suite
Consulting
Leverage our experience to build strategies for growth
Cloud as a Service
Consume services from cloud platforms securely
Helpdesk & Support
We are committed to enhancing the support experience by going beyond traditional helpdesk services, implementing a robust process that empowers our clients and enables our agents to operate with peak efficiency.
Backup & DRP
Don't leave anything to chance. Our experts will devise a customised business continuity plan for your business.
Security Policies and Compliance
IT Governance and Risk Management baked into service
Security Fundamentals
What is Zero Trust Architecture (ZTA)
NIST zero trust architecture (ZTA) is a set of cybersecurity principles that move defenses from static, network based perimeters to focus on users, assets, and resources. It enables secure authorized access to enterprise resources that are distributed across on-premises and multiple cloud environments, while enabling a hybrid workforce and partners to access resources from anywhere, at any time, from any device in support of the organization’s mission.
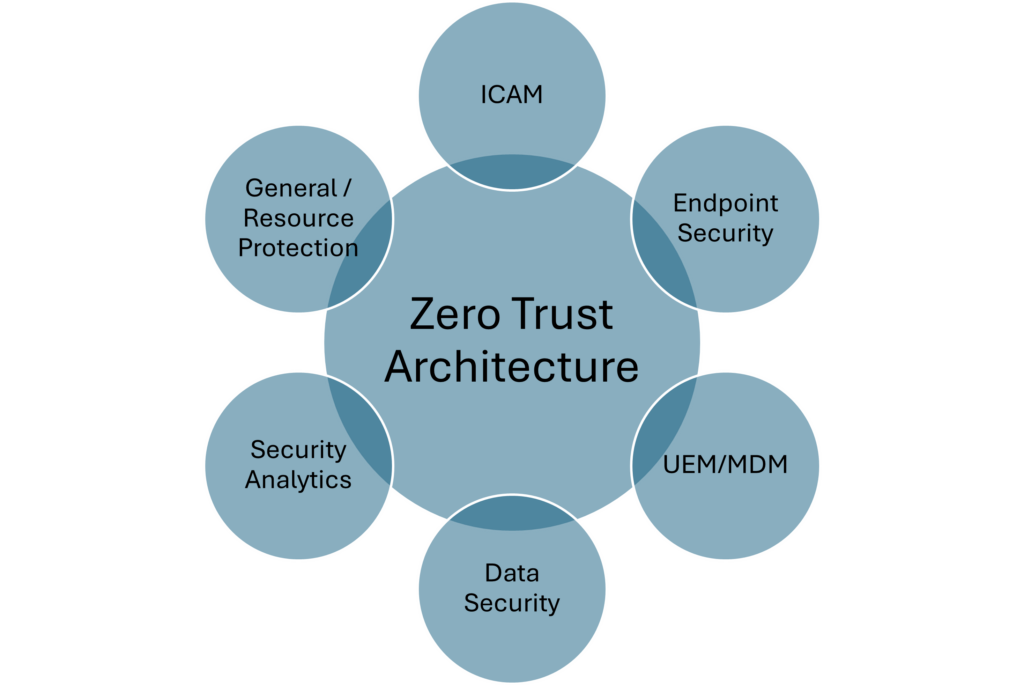
Microsoft SAF Principles
We embrace the Microsoft Security Architecture Framework (SAF), exemplified by Microsoft’s innovative product families. Microsoft SAF describes Microsoft’s cybersecurity capabilities and technologies and maps them to the Microsoft product family.
SAF provides guidance for organizations through end-to-end security modernization across a ‘hybrid of everything’ multicloud and multi-platform technical estate.

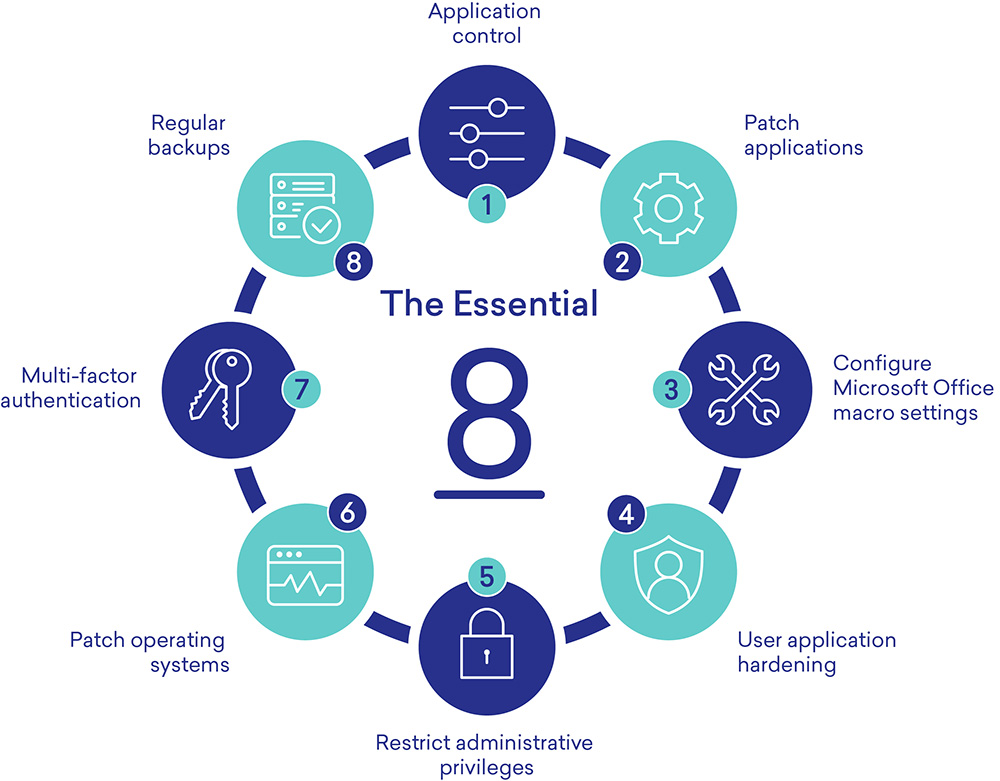
ASD Essential Eight
The Australian Signals Directorate (ASD) Essential Eight is a set of prioritized cyber mitigation strategies, to assist organizations protect themselves against various cyber threats.
The mitigation strategies that constitute the Essential Eight are:
- patch applications
- patch operating systems
- multi-factor authentication
- restrict administrative privileges
- application control
- restrict Microsoft Office macros
- user application hardening
- regular backups.
Protect your business from cyber threats TODAY !
Protection against cyber threats both visible and those hidden “outside the flags !”