
Discover, monitor, and enforce comprehensive protection against cyber threats with Hunto’s SaaS-based Digital Attack Surface Management (DASM) platform.
Our approach offers complete life cycle protection from a broad range of external threats that are based on a three-phased approach of discovery, monitoring and enforcement.
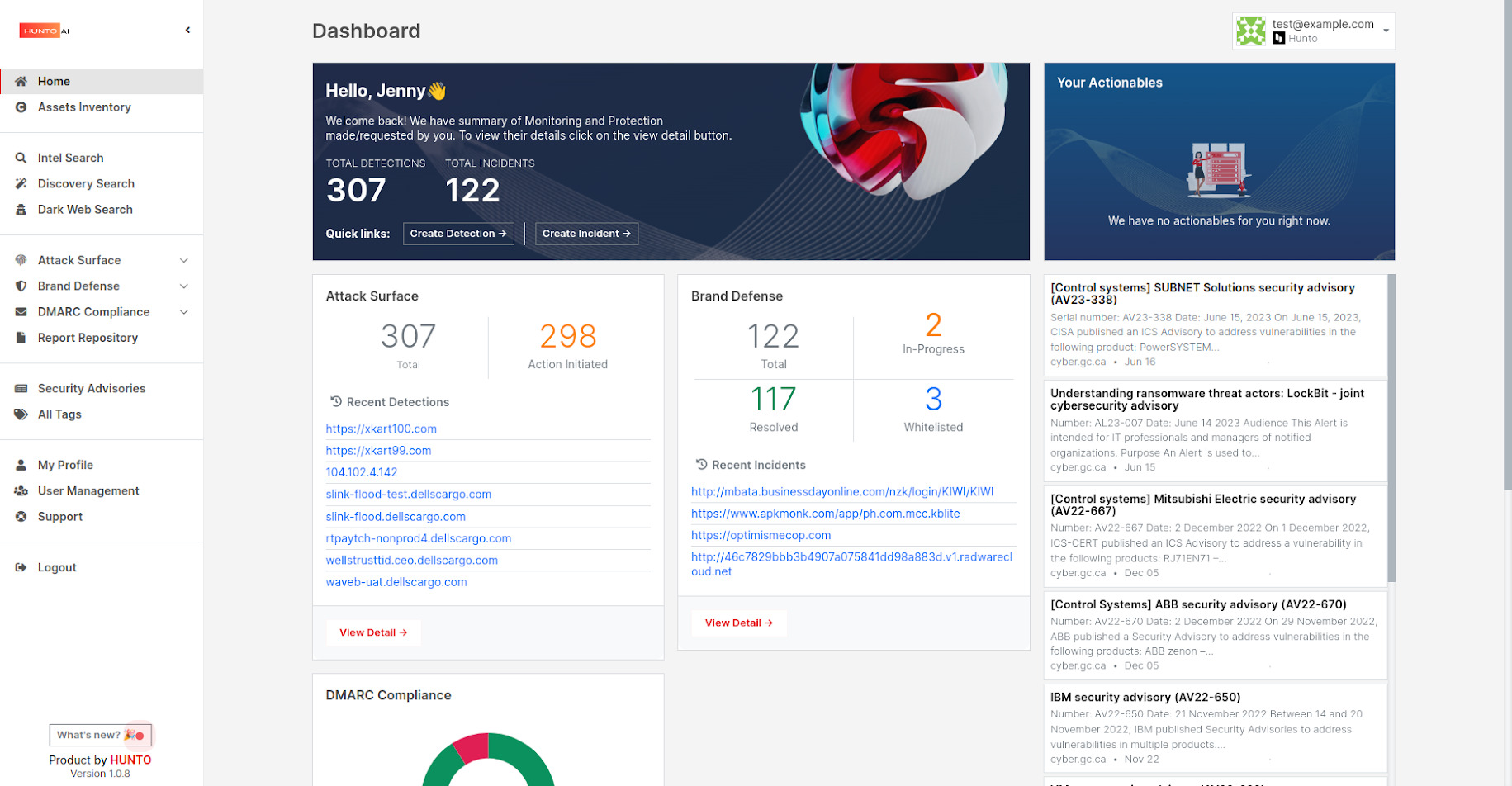
Hunto ASM solution offers a comprehensive, proactive, and adaptive approach to managing and securing an organization’s ever-evolving digital footprint.
Built on four key pillars, Hunto provides comprehensive visibility of external threats targeting your organization.
1. Digital Attack Surface Monitoring
2. Brand Defense
3. DMARC Compliance
4. Deep and Dark Web Monitoring
Protection against cyber threats both visible and those hidden “outside the flags !”
You can see how this popup was set up in our step-by-step guide: https://wppopupmaker.com/guides/auto-opening-announcement-popups/
Attacks have increased tremendously during COVID 19.
Are you under attack? Report COVID 19 Scam